32 AntiVirus versus the latest Java Exploit (CVE-2013-1493)
Image a scenario where someone wants to target your computer to get access to your files. This task can be accomplished in several ways and one of them is using a java exploit on a crafted/compromised website.
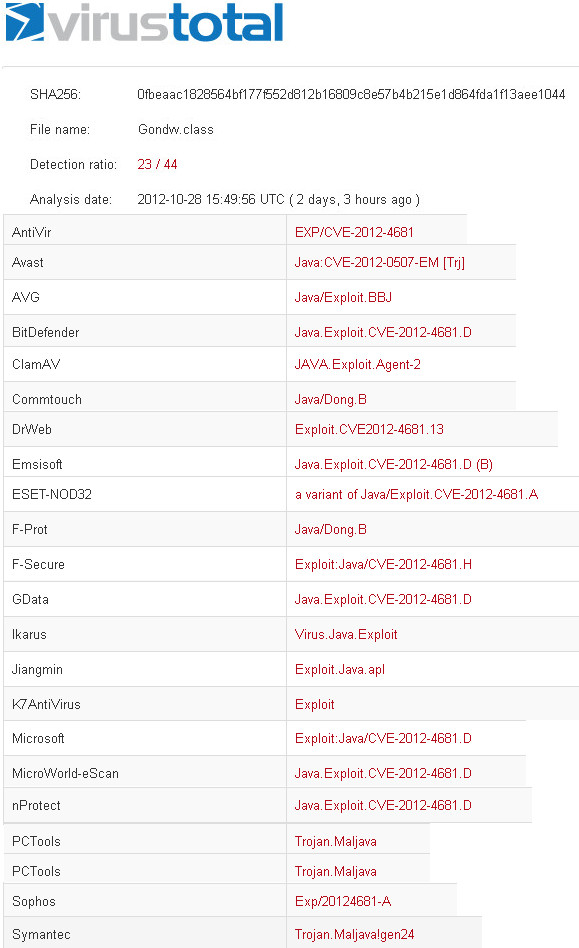
What i want to test is how AntiVirus manage "unknown" threads or forbidden behavior (an unsigned applet shouldn't be allowed to download files to your local disk).
This test is based on basic/home/free products like Symantec AntiVirus and not Symantec Internet Security which has more features. Some companies provide only Internet Security suites so this cannot be a fully comparison between these products.
I tried to test all AntiVirus in this list but i came out with only 32, because some of them don't provide a free trial and the others i was unable to find it or install it. The important thing is that i covered all major/popular AntiVirus.
Testing machine is a Windows 7 SP1 32 bit fully patched on Virtualbox with Java SE 7 update 15 and as browser Firefox.
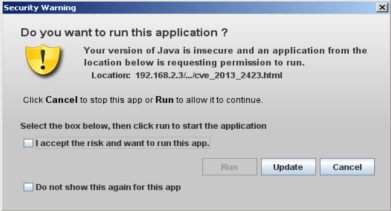
The exploit is CVE-2013-1493 not obfuscated that after a successfully exploitation tries to download from a remote host to temp directory hello.jpg , after that the is renamed to hello.exe and executed using cmd "cmd /C 'temp_path\hello.exe'".
The executable just prompt "Hello Malware".
I decided to run this executable instead of the classic calculator because some AntiVirus have cloud based reputation service and since this is an unknown file dropped by java (like malware) they should prompt some warning.
Maybe someone of you will say "this is not a malware, of course av doesn't block it", what i want to test here is the software against the java exploit not about malicious executable detection, because this is another story.
Developers of chk4me claim to not send uploaded files to AntiVirus companies so this is the right place to check the exploit before the test.
To be more clear i made this table where i report the "score" obtained by the AntiVirus against CVE-2013-1493.
I used this scale of values:
Summarizing the results:
There were some cases where i was undecided between the score 1 or 2, like the case of ArcaVir. When an applet tries to contact another domain ArcaVir prompt you an alert, however its not saying "this is an exploit and i block it" but "hey, this applet is trying to connect to this domain, what you wanna do ?". For this reason i opted for a score of 1 instead of 2.
Symantec surprised me because a couple of months ago didn't detect any java exploit and now they block it all, maybe they have decided to improve their basic software after the Wall Street Journal story.
As last thing here is the video, maybe you will find it boring but you can see how several antiviruses handles a java exploit.
What i want to test is how AntiVirus manage "unknown" threads or forbidden behavior (an unsigned applet shouldn't be allowed to download files to your local disk).
This test is based on basic/home/free products like Symantec AntiVirus and not Symantec Internet Security which has more features. Some companies provide only Internet Security suites so this cannot be a fully comparison between these products.
I tried to test all AntiVirus in this list but i came out with only 32, because some of them don't provide a free trial and the others i was unable to find it or install it. The important thing is that i covered all major/popular AntiVirus.
Testing machine is a Windows 7 SP1 32 bit fully patched on Virtualbox with Java SE 7 update 15 and as browser Firefox.
The exploit is CVE-2013-1493 not obfuscated that after a successfully exploitation tries to download from a remote host to temp directory hello.jpg , after that the is renamed to hello.exe and executed using cmd "cmd /C 'temp_path\hello.exe'".
The executable just prompt "Hello Malware".
Maybe someone of you will say "this is not a malware, of course av doesn't block it", what i want to test here is the software against the java exploit not about malicious executable detection, because this is another story.
Developers of chk4me claim to not send uploaded files to AntiVirus companies so this is the right place to check the exploit before the test.
To be more clear i made this table where i report the "score" obtained by the AntiVirus against CVE-2013-1493.
I used this scale of values:
- 0 = Exploit and "malicious" exe executed successfully
- 1 = Exploit executed successfully but "malicious" exe not executed or sandboxed
- 2 = Exploit blocked/not executed
| AntiVirus Name | Score |
|---|---|
| Ad-Aware Free Antivirus+ | 0 |
| AVG Antivirus Free 2013 | 0 |
| Avira Free Antivirus 2013 | 0 |
| Bitdefender Antivirus Free Edition | 0 |
| Quick Heal Antivirus Pro 2013 | 0 |
| Immunet 3.0 | 0 |
| Dr.Web Anti-virus Pro | 0 |
| ESET NOD32 Antivirus 6 | 0 |
| FortiClient Endpoint Security Management | 0 |
| F-PROT Antivirus | 0 |
| F-Secure Anti-Virus | 0 |
| G Data AntiVirus 2013 | 0 |
| IKARUS anti.virus | 0 |
| Kingsoft Internet Security 9 | 0 |
| Malwarebytes Anti-Malware Free | 0 |
| McAfee AntiVirus Plus 2013 | 0 |
| Microsoft Security Essentials | 0 |
| NANO Antivirus | 0 |
| Norman Antivirus 10 | 0 |
| Outpost Antivirus Pro | 0 |
| Panda Cloud Antivirus | 0 |
| Rising Free Antivirus | 0 |
| VIPRE Antivirus 2013 | 0 |
| VirusBuster Personal Antivirus | 0 |
| ArcaVir 2013 Antivirus | 1 |
| Avast! Free Antivirus | 1 |
| Comodo Antivirus Free | 1 |
| Emisoft Anti-Malware 7.0 | 1 |
| Trend Micro Titanium Antivirus Plus | 1 |
| Kaspersky Anti-Virus 2013 | 2 |
| Norton AntiVirus | 2 |
| Sophos Anti-Virus | 2 |
Summarizing the results:
- 24 (75 %) don't detect the exploit neither the executable
- 5 (16 %) don't detect the exploit but they warn you about the executable
- 3 (9 %) detect the exploit.
There were some cases where i was undecided between the score 1 or 2, like the case of ArcaVir. When an applet tries to contact another domain ArcaVir prompt you an alert, however its not saying "this is an exploit and i block it" but "hey, this applet is trying to connect to this domain, what you wanna do ?". For this reason i opted for a score of 1 instead of 2.
Symantec surprised me because a couple of months ago didn't detect any java exploit and now they block it all, maybe they have decided to improve their basic software after the Wall Street Journal story.




Comments
Post a Comment