Styxy Cool Exploit Kit: One Applet to Exploit All Vulnerabilities

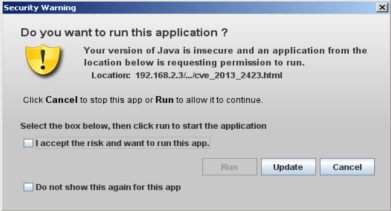
Styxy Cool Exploit Kit is a particular kit because it is a "merge" between Cool and Styxy Exploit Kit. Here we are going to cover only Java related exploits so, if you want to know what vulnerabilities it has and why its called Styxy Cool go check Kafeine's post here . Between the eight and nine of July two interesting things happened: Jar size increased from 5Kb to 28 Kb Payload (Reveton) disappeared from fiddler Let's take a step back and analyze the exploit chain from the eight of July. The first page /abortion-success_conductor.php displays a bounch of phrases about Yahoo France, but what really does is checking if you have some vulnerable Java plugin installed in your browser. The page contains an instance of PluginDetect version 0.8 plus an obfuscated JavaScript code. What does this code do ? It takes the content of the textarea from / objection_confident_sulphur.html since in the middle of the first page there is an iframe pointin...