From XSS to NT AUTHORITY
A lot of times i have seen Cross-site scripting vulnerabilities classified as low impact or not significant. Thus, this time i want to show you how an attacker can get administration privileges through a simple XSS.
A couple of months ago i discovered an XSS vulnerability affecting the uk website of Orange http://www.orange.co.uk. I've emailed them a month ago (and two weeks ago) regarding this vulnerability, but i haven't received any response yet.
From wikipedia:
When you read an article, for example this one obesity_levels_could_be_cut_with_20_fat_tax, you can see the users comments at the bottom of the page. If a user want to leave a comment, he must log in via google, facebook etc.... Once logged, the website create a profile with all your statictis (recent comments) and personal information (age, gender, joined).
If you click on the name of a user you will be redirected to his profile page like this below.
If you take a look at the url you will see that it has three parameters:
hxxp://web.orange.co.uk/r/community/persona?UID=)("><'/&\
Surprisingly we get this
Oh... we are lucky; at the first attempt we have obtained something interesting. Let's try with a bit of html code.
As expected the page didn't sanitize the output interpreting the html code. Using firebug we can see in which part of the page is located the faulty parameter.
Now we sobstitute the h1 tag with a script tag (<script>alert(0)</script>) and we should get an alert box.
Is not so, let's take a look at the source code.

Seems there is an XSS filters with some blacklist tags. There are tons of others ways to trigger an XSS without a script tag, one of them is using the img tag.
<img/src="1"/onerror="alert(1)"
Since 1 isn't a valid image the onerror event is triggered and his content executed. Now all we have to do is sobstitute the alert instruction with some useful code.
In our case we want to redirect the victim to a cloned page containing a malicious java applet, so the code will be:
How can we trick the victim to click our malicious link ?
Simple, we can send him an email regarding some promotions that orange actually do and telling to click on the image.
But here we have a little problem.
When you place the mouse over the image in most of the browsers at the bottom will appear the link pointed by the image. Some users can be suspicious viewing a link like this hxxp://web.orange.co.uk/r/community/persona?UID="><img/src="1"/onerror="window.location='...'", so disguise the url is a necessary step.
To accomplish this task we do two things:
And the result is this.
To compromise victim's machine we use a great feature from SET called Java Applet Attack Vector.
From http://www.social-engineer.org:
That's all, enjoy the video.
A couple of months ago i discovered an XSS vulnerability affecting the uk website of Orange http://www.orange.co.uk. I've emailed them a month ago (and two weeks ago) regarding this vulnerability, but i haven't received any response yet.
From wikipedia:
Orange is the flagship brand of the France Telecom group for mobile, landline and Internet businesses, with 226 million customers as of December 2011 and, under the brand Orange Business Services, is one of the world.How i found this XSS ?
When you read an article, for example this one obesity_levels_could_be_cut_with_20_fat_tax, you can see the users comments at the bottom of the page. If a user want to leave a comment, he must log in via google, facebook etc.... Once logged, the website create a profile with all your statictis (recent comments) and personal information (age, gender, joined).
If you click on the name of a user you will be redirected to his profile page like this below.
If you take a look at the url you will see that it has three parameters:
- UID
- plckUserId
- plckPersonaPage
hxxp://web.orange.co.uk/r/community/persona?UID=)("><'/&\
Surprisingly we get this
Oh... we are lucky; at the first attempt we have obtained something interesting. Let's try with a bit of html code.
As expected the page didn't sanitize the output interpreting the html code. Using firebug we can see in which part of the page is located the faulty parameter.
Is not so, let's take a look at the source code.

Seems there is an XSS filters with some blacklist tags. There are tons of others ways to trigger an XSS without a script tag, one of them is using the img tag.
<img/src="1"/onerror="alert(1)"
Since 1 isn't a valid image the onerror event is triggered and his content executed. Now all we have to do is sobstitute the alert instruction with some useful code.
In our case we want to redirect the victim to a cloned page containing a malicious java applet, so the code will be:
How can we trick the victim to click our malicious link ?
Simple, we can send him an email regarding some promotions that orange actually do and telling to click on the image.
But here we have a little problem.
When you place the mouse over the image in most of the browsers at the bottom will appear the link pointed by the image. Some users can be suspicious viewing a link like this hxxp://web.orange.co.uk/r/community/persona?UID="><img/src="1"/onerror="window.location='...'", so disguise the url is a necessary step.
To accomplish this task we do two things:
- Add unexisting url parameters ( page=1&category=2&ticket=24234&session_id=888 )
- XSS character encoding ( UID="><img ... to %55%49%44=%22%3E%3C%69%6D%67.... )
And the result is this.
To compromise victim's machine we use a great feature from SET called Java Applet Attack Vector.
From http://www.social-engineer.org:
The Java Applet is one of the core attack vectors within SET and the highest success rate for compromise. The Java Applet attack will create a malicious Java Applet that once run will completely compromise the victim. The neat trick with SET is that you can completely clone a website and once the victim has clicked run, it will redirect the victim back to the original site making the attack much more believable.I've cloned this page hxxp://web.orange.co.uk/p/film/cinema_tickets and sent the email with a address that a lot of companies uses when they send promotions and things like that (donotreply@...).
That's all, enjoy the video.










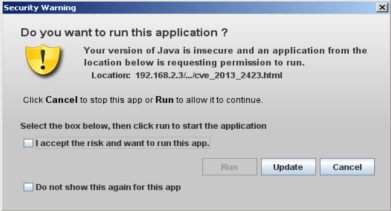

So, the XSS vulnerability was just used to make the link more authentic looking?
ReplyDeleteIf I am right you could cloak the link a million other ways (URL shortener for example). Why bother with the XSS hassle?
Or am I missing something here?
Greetings
The XSS hassle allows the malicious payload to be delivered in a response from a genuine, trusted site – this is very different from a scenario where the attacker attempts to induce the victim to click on an obscure (e.g. shortened) URL. Here, the URL does not just look authentic – it actually points to the real site operated by Orange.
DeleteAnonymous gave you a good explanation.
DeleteThank you. This makes it clear to me.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteThank you
DeleteOut of interest, what orange email did you disclose this to?
ReplyDeleteNone, as i wrote a lot of companies uses donotreply as their email address to send advertisement etc...
DeleteBut orange uses dontreply instead of donotreply.
I think the previous comment was related to your statement:
Delete"A couple of months ago i discovered an XSS vulnerability affecting the uk website of Orange http://www.orange.co.uk. I've emailed them a month ago (and two weeks ago) regarding this vulnerability, but i haven't received any response yet."
i.e. Who did you originally e-mail to disclose the vulberability?
To this e-mail address: webmaster@orange.co.uk
DeleteThis comment has been removed by a blog administrator.
ReplyDeleteVery good video and skills
ReplyDelete