ARP/DNS Spoofing Steal Facebook Password (LAN Environment)
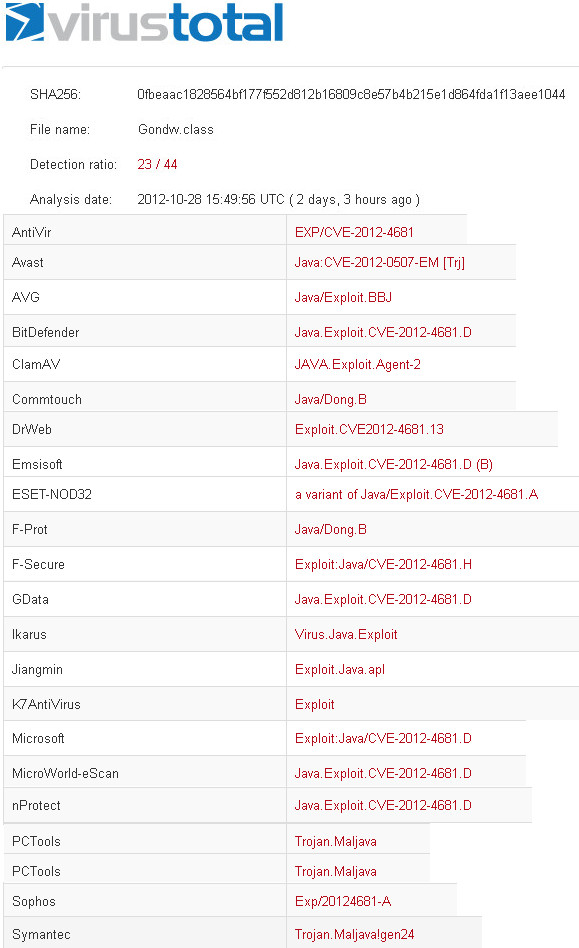
In this video i'll show you how an attacker can steal user credentials of every site (in this case will be facebook) in a LAN environment. First of all we use SET to clone the current facebook home page and setup a server listening on port 80 with that copy.
Next step is to discover potential victims mapping our network. There are tons of ways to do this through nmap, hping, ping command, but this time i used the linux command arp-scan with the following syntax:
After mapping the network i used a great tool called netcmd to perform an arp spoofing attack to redirect traffic through the attacker.
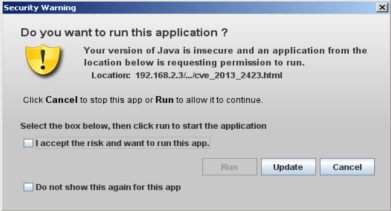
Last step is to perform a dns spoofing attack so all request sent by the victim to facebook.com will be redirected to the attacker. To do this we need to use ettercap and modify /usr/share/ettercap/etter.dns adding this two lines.
After lunched ettercap we have just to wait for the victim to login into his facebook account.
Enjoy the video.
Next step is to discover potential victims mapping our network. There are tons of ways to do this through nmap, hping, ping command, but this time i used the linux command arp-scan with the following syntax:
After mapping the network i used a great tool called netcmd to perform an arp spoofing attack to redirect traffic through the attacker.
Last step is to perform a dns spoofing attack so all request sent by the victim to facebook.com will be redirected to the attacker. To do this we need to use ettercap and modify /usr/share/ettercap/etter.dns adding this two lines.
After lunched ettercap we have just to wait for the victim to login into his facebook account.
Enjoy the video.




Comments
Post a Comment