The Latest Java Exploit with Security Prompt/Warning Bypass (CVE-2013-2423)
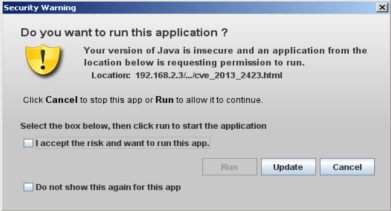
From Java SE 7 update 11 oracle has introduced a new security features called security warning that prompts a window every time an applet request for execution. For example, if we want to execute latest Java SE 7 update 17 exploit we get this warning. Yesterday Immunity has published a blog post explaining a new vulnerability they have found into the java validating mechanism which allow to execute an untrusted applet without showing the warning. For in-dept details read their blog post here . Briefly, to bypass the above prompt you must call the applet with the parameter __applet_ssv_validated set to true. The only way to manipulate this parameter is to use a java Network Launch Protocol file. Regarding to oracle there are two ways to use JNLP in a page: With the applet tag With javascript only Let's try first the example with the tag applet. The code we're going to run is the latest publicly available java exploit CVE-2013-2423 . import java.a...