Attacking Windows 8 with Java Exploit and Metasploit

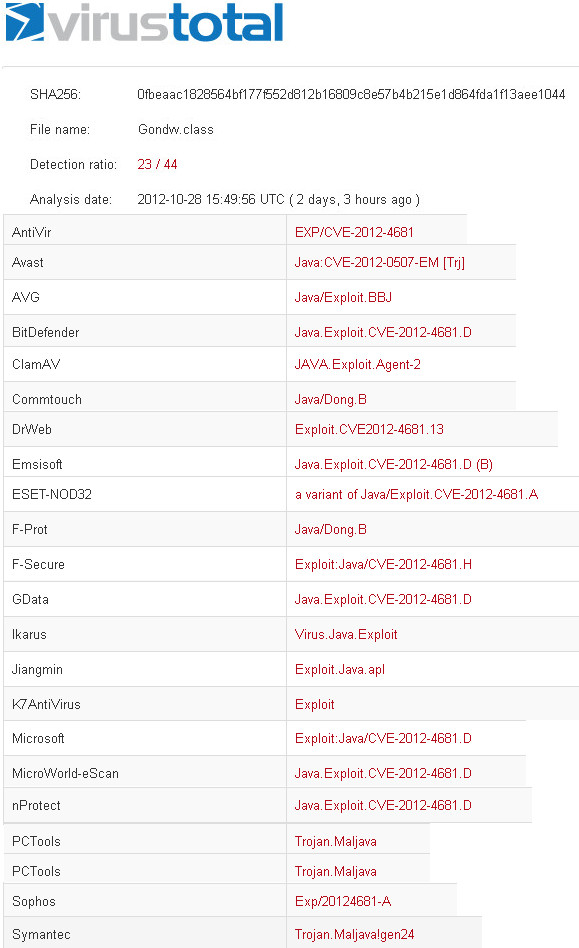
In the last post i was talking about how to obfuscate a Java exploit (CVE-2012-4681 link here ), now i want to show you how an attacker can use this obfuscated exploit for a targeted attack. This is intended to be the second part of Wordpress Cookie Grabber video because i will show what you can do once you have compromised a website, frank's blog in this case. The victim will be only the administrator. The exploit code in the previous article just escape from java sandbox and launch windows calculator. What we want to do is launch something different, like a meterpreter reverse shell which will connect back to the attacker. Thus in the previous code we have to add a download & execute class/method. I opted for a new class but you can certainly add a method in the same class. This new class called NewClass (i'm lacking of fantasy) will download a meterpreter executable from a remote host and save it with the name fsc73B8.tmp.exe into temp folder, after t...