Java Exploit Code Obfuscation and Antivirus Bypass/Evasion (CVE-2012-4681)
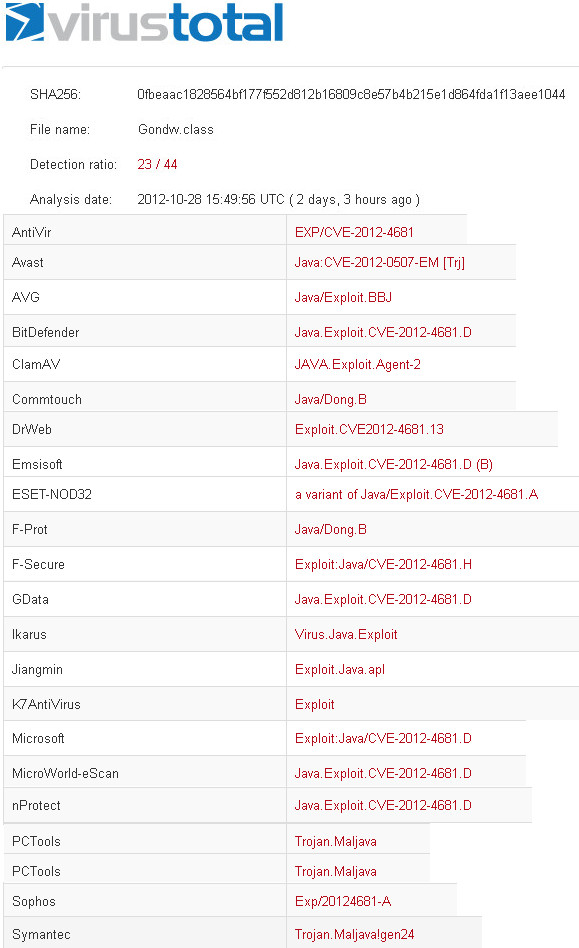
Why not play a game where we try to make the latest (at time of writing) public java exploit ( CVE-2012-4681 ) undetected by all antivirus and see who will be the last to detect it ?. I think it will be a funny "challenge" because evading antivirus has always his charm. I will not use software obfuscators like proGuard, Allatori, Zelix KlassMaster etc... This because will not be funny. This is not intended to be an analysis or explanation because there are already great post here: http://immunityproducts.blogspot.com.ar/2012/08/java-0day-analysis-cve-2012-4681.html http://www.deependresearch.org/2012/08/java-7-vulnerability-analysis.html http://www.h-online.com/security/features/The-new-Java-0day-examined-1677789.html Before we start we need to make two considerations: From The Current Web-Delivered Java 0Day : So while you may see a few links to Virustotal with the inevitable complaining that a scanner is missing a specific chunk of altered code along with innacc
